DDoS Attacks in the Age of IoT: Risks and Solutions
The Internet of Things (IoT) has transformed how you live, work, and interact. IoT devices, from connected cars to smart homes, are becoming integral to your daily lives. However, this increased use of connected devices also brings significant cybersecurity risks. Distributed Denial of Service (DDoS) attacks are becoming quite prevalent.
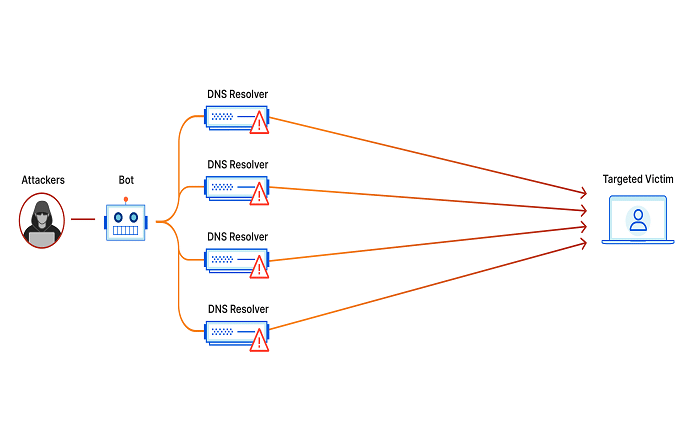
A DDoS attack is a malicious attempt to disrupt the regular traffic of a targeted server. It is done by overwhelming it with a flood of internet traffic. It is achieved by leveraging multiple compromised computer systems as sources of traffic. The result is a significant slowdown or complete outage of the targeted resource. Let’s understand all about it in this article.
The Rise of Such Attacks in the IoT Era
As IoT devices grow, so do the opportunities for cybercriminals to exploit them. Many devices lack robust security measures, making them easy targets for hackers. The sheer number of IoT devices means that even a tiny percentage of compromised devices can create a massive botnet capable of causing significant disruption.
Wondering why IoT devices are vulnerable? Here’s why:
- Lack of Security Protocols: Many devices are designed with convenience and cost in mind, often at the expense of security. Default passwords, unencrypted communications, and outdated software make these devices easy targets.
- Limited Computing Power: The limited computing power of many devices makes it challenging to implement robust security measures. This makes it easier for hackers to gain control over them.
- Rapid Growth and Deployment: The rapid expansion of devices means that security often takes a backseat in the rush to market. This results in devices being deployed with known vulnerabilities.
Real-World Impact
The impact of such attacks can be quite far-reaching, affecting both businesses and individuals. These attacks can cause significant downtime for websites and online services. It can end up leading to lost revenue and reputational damage.
Sometimes, these are used as a smokescreen to divert attention while hackers infiltrate systems to steal sensitive data. Businesses may also incur significant costs in mitigating attacks, from investing in security infrastructure to paying for additional bandwidth to handle traffic spikes.
Mitigating Attacks: Effective Strategies
While the threat of such attacks in the age of IoT is real, there are several strategies that organisations and individuals can employ to protect themselves:
- Robust Network Security: Implementing robust network security measures, such as firewalls, intrusion detection systems, and anti-DDoS technologies, can help mitigate the risk of attacks.
- Regular Updates and Patches: Keeping IoT devices updated with the newest security patches is crucial in closing known vulnerabilities.
- Strong Authentication: Using strong, unique passwords and enabling multi-factor authentication can help protect IoT devices from being compromised.
- Traffic Analysis: Monitoring network traffic for unusual patterns can help identify potential attacks before they cause significant damage.
Personal Steps to Enhance Security
For individuals, taking a few simple steps can go a long way in protecting personal IoT devices:
- Change Default Settings: Always change default passwords and disable unnecessary features that hackers could exploit.
- Secure Your Network: Use robust encryption protocols for your home network and consider segmenting your IoT devices on a separate network.
- Be Aware of Data Sharing: Be mindful of the data your IoT devices collect and share, and disable any unnecessary data collection features.
While the age of IoT brings unparalleled convenience and connectivity, it also introduces significant cybersecurity challenges. Manufacturers must prioritise security in designing and deploying IoT devices, and consumers must be vigilant in protecting their devices.
Collaboration between industry stakeholders, regulatory bodies, and cybersecurity experts is essential to developing comprehensive solutions to reduce the risks associated with such attacks. By understanding the dangers and incorporating effective security measures, you can enjoy the advantages of IoT while minimising the threat of a DDoS attack. Continuous adaptation is critical to staying one step ahead of cybercriminals as technology changes.